WireGuard can be used for a lot of things:
- Managing router configuration remotely behind NATed networks such as mobile connections.
- Connecting to your home network while on the road for home automation and safe internet access.
- Connecting several networks over the public internet.
This post focuses on enabling remote access to Mikrotik routers and the attached networks. All other setups are outside the scope of this document and can be designed by following this awesome WireGuard documentation.
Mikrotik added official support for WireGuard in version 7 of RouterOS.
Peers, Servers and Clients
With WireGuard everything is a “peer” which often causes confusion about how to configure each device on the network.
In practice, most consumer devices today are on some kind of private ISP network and can’t be addressed from the public internet which is good for security reasons. Only when your device initiates a connection to a remote service such as google.com (a TCP connection), do all of the routers on the way establish a connection path back to your device. This is called Network address translation or NAT.
That is why most WireGuard networks require at least one “peer” with a real public IP address that is accessible on the public internet to serve as a gateway. Accessing peers behind NATed connections such as mobile phones and most home internet connections isn’t possible without connecting through a peer on the public internet unless you want to attempt some kind of UDP hole punching.
This article assumes the following network elements:
- One WireGuard peer on the public network serving as a gateway for the rest of the peers.
- One MikroTik router configured as a WireGuard peer.
WireGuard Gateway or Server Peer
This can be any computer with a public IP address running Wireguard. There are many guides for how to build one on DigitalOcean, Linode, AWS or any other cloud hosting provider. Alternatively, use one of the commercial offering but keep in mind that anyone with access to the private keys of your peers can access your WireGuard network.
For our example we’ll use the following server configuration:
- Public IP
123.123.123.1 - WireGuard
ListenPortset to 51820 - WireGuard
Addressrange set to10.100.100.1/24 - WireGuard public key
YrXqKGpYLVx829MCcVcb78QFDWIeeWfOyFHmdmZAlF0=
Assuming that the server is up and running, let’s configure the WireGuard peer on RouterOS.
MikroTik as a WireGuard Peer
Under the “WireGuard” menu we first create a new WireGuard network interface that defines this MikroTik peer to the rest of the network:
Create New WireGuard Interface
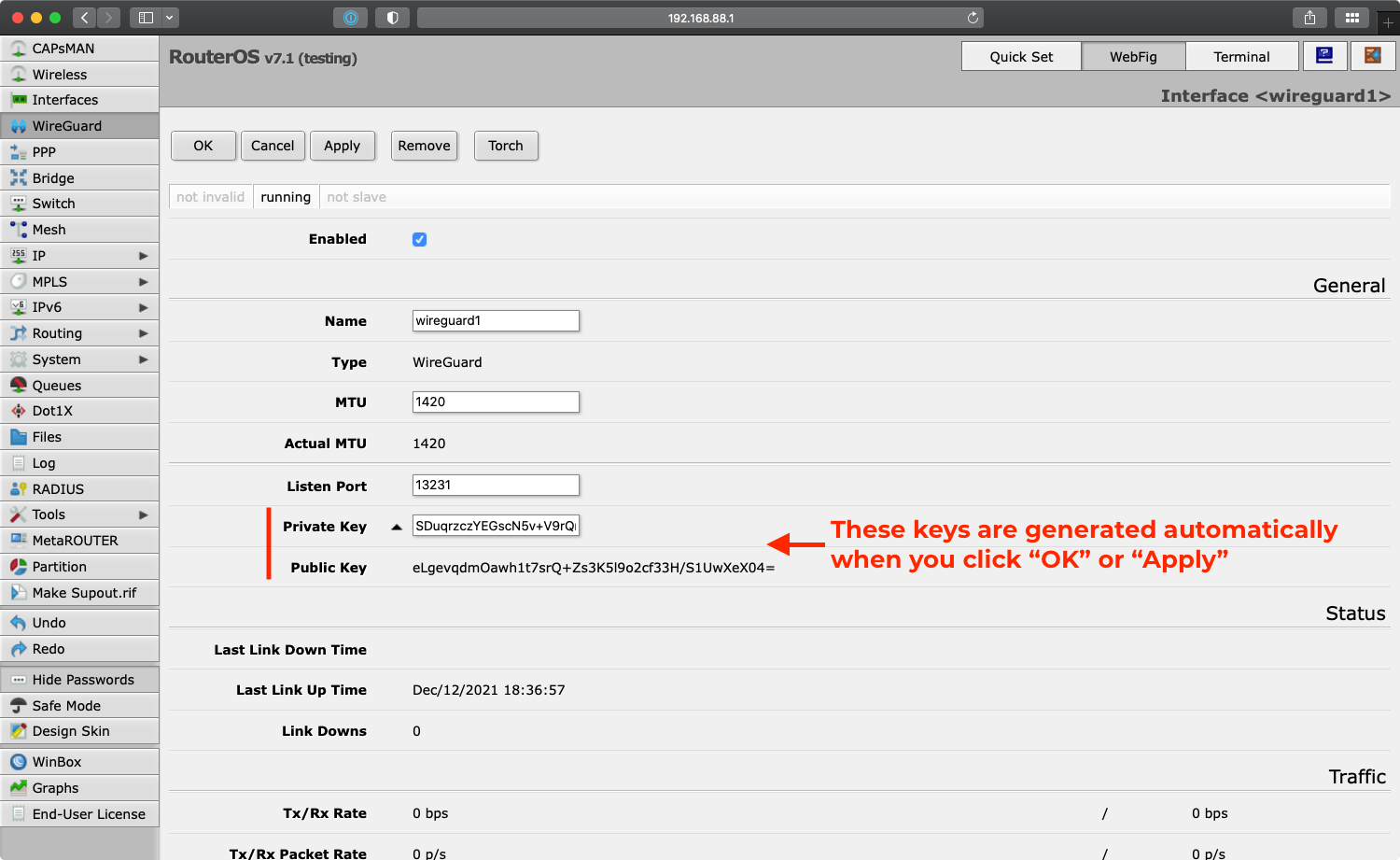
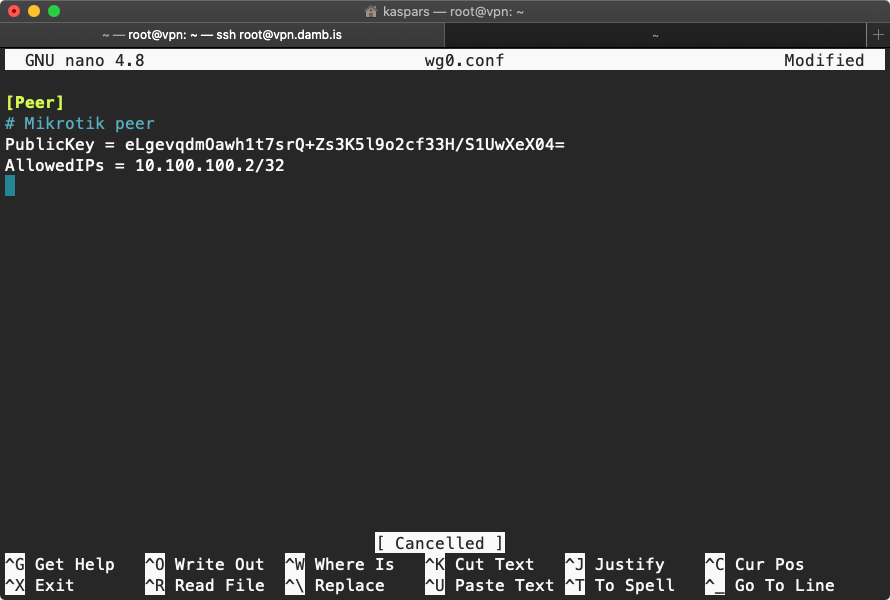
After clicking “OK” or “Apply” it generates the private and public keys that are required for adding this peer to the network. Note down the public key eLgevqdmOawh1t7srQ+Zs3K5l9o2cf33H/S1UwXeX04= as it is needed later for adding the router to the gateway server.
Define Gateway Peer Connection
Under the “Peers” tab add the details for the connection to the gateway server:
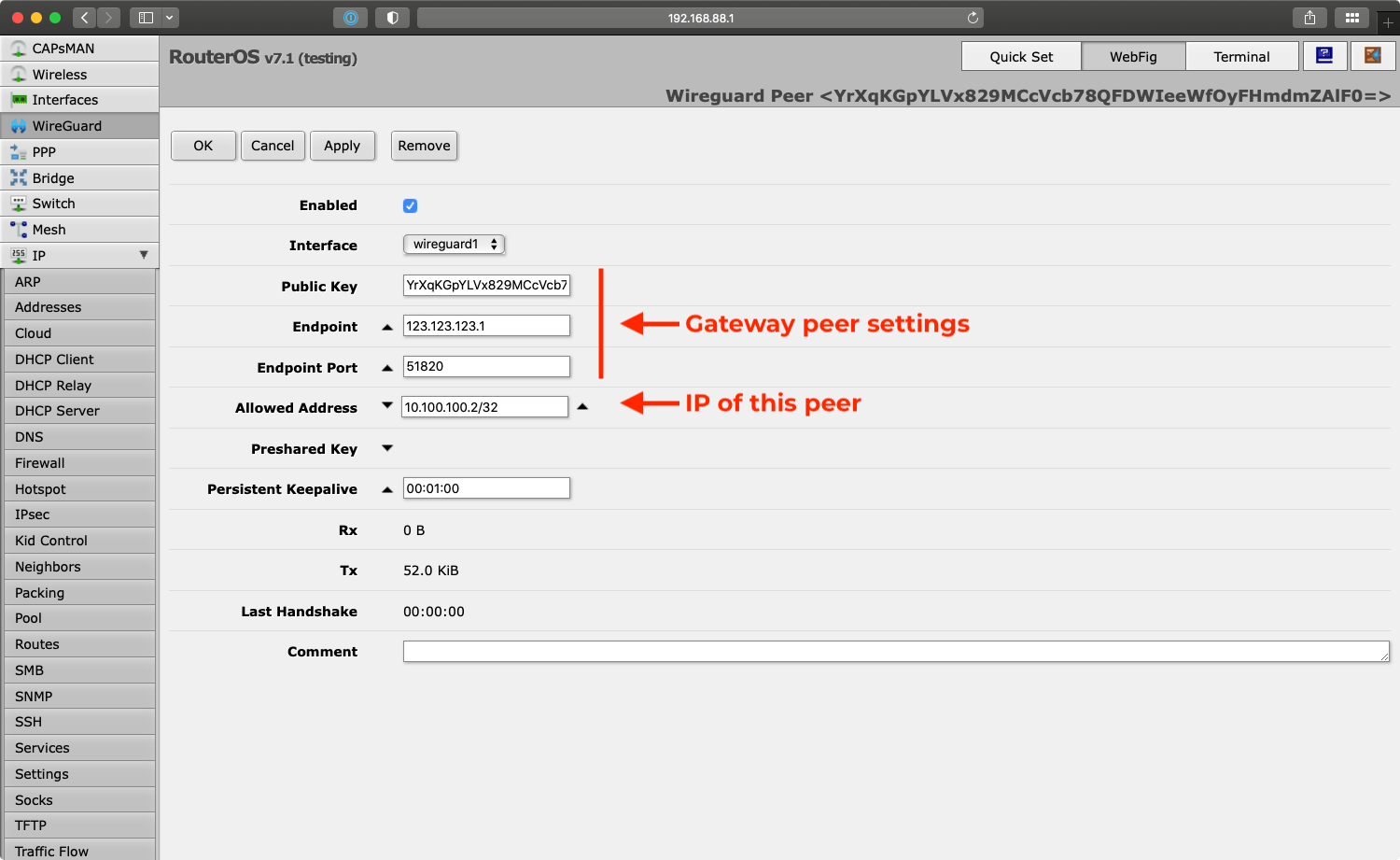
Public Key, Endpoint and Endpoint Port are all values of our gateway server described above. The only unique value is the “Allowed Address” which we assign to 10.100.100.2/32.
Optionally configure the “Persistent Keepalive” to ensure it keeps the connection information updated with the gateway when the ISP assigned IP changes.
Add MikroTik Peer to the Gateway Configuration
We need to make the Gateway server aware of the newly created peer, so we update its configuration to include the new peer:
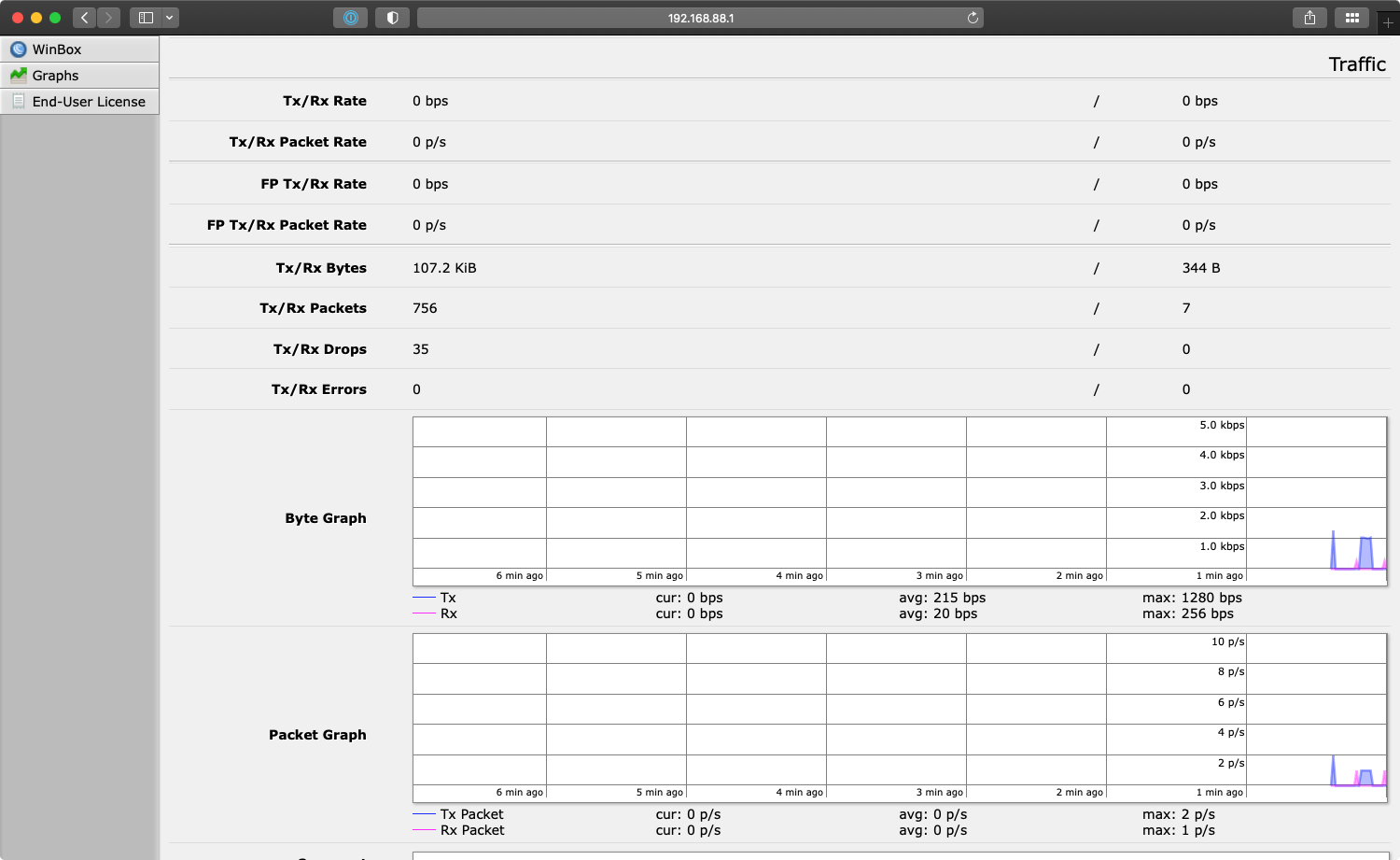
After restarting the WireGuard interface on the gateway server, the MikroTik traffic monitor for the WireGuard interface should start showing keep-alive and handshake data flowing:
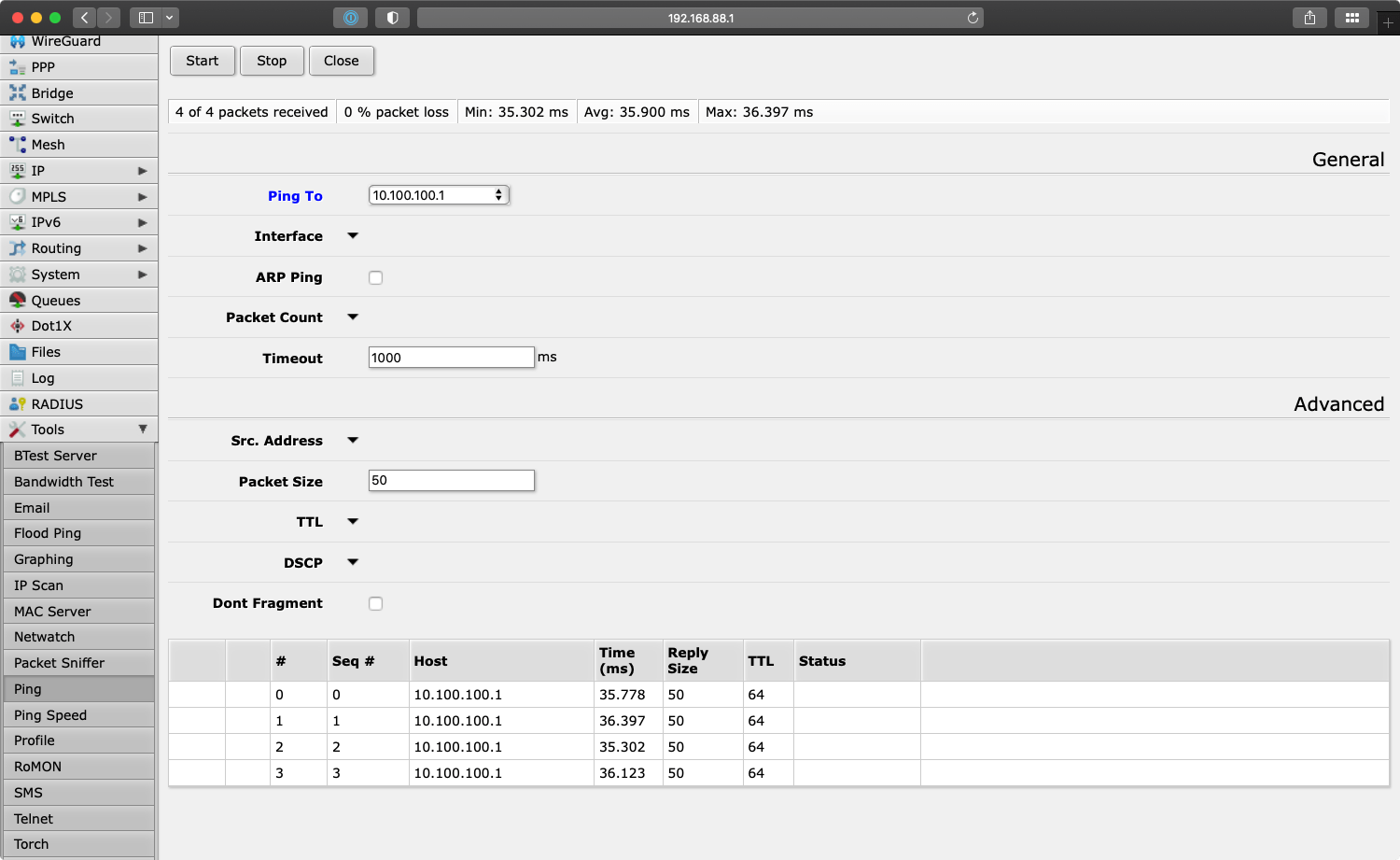
At this point the MikroTik router should be able to ping the WireGuard network:
However, nothing has been configured about how the newly created interface can be reached from the outside or inside the MikroTik network.
To make the WireGuard network accessible from the local 192.168.88.0/24 network, we must first define its address range and routing information.
Define WireGuard Peer IP and Routes
To make the router aware of its new IP address on the WireGuard network, go to “IP > Addresses” and add the address 10.100.100.2/24:
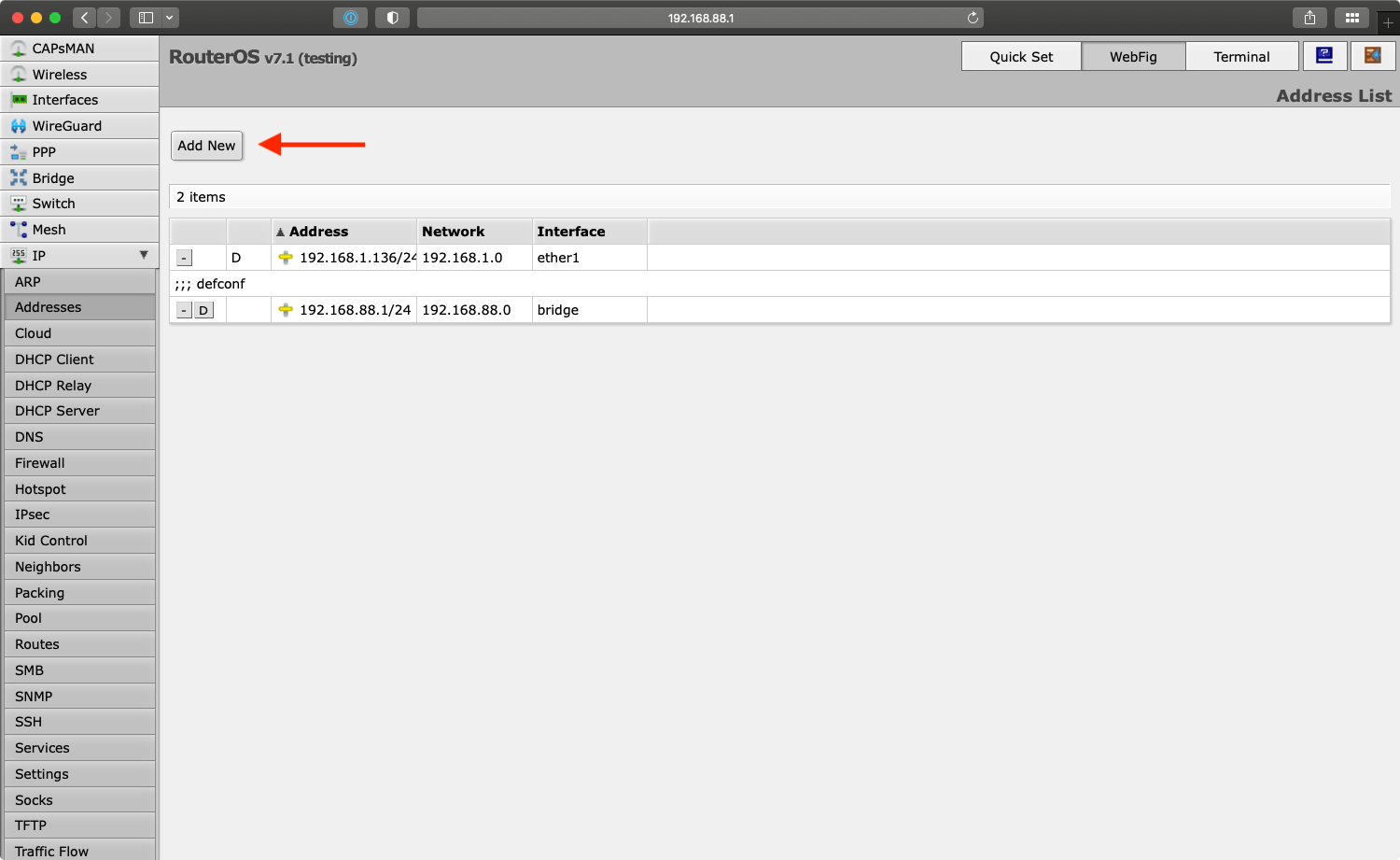
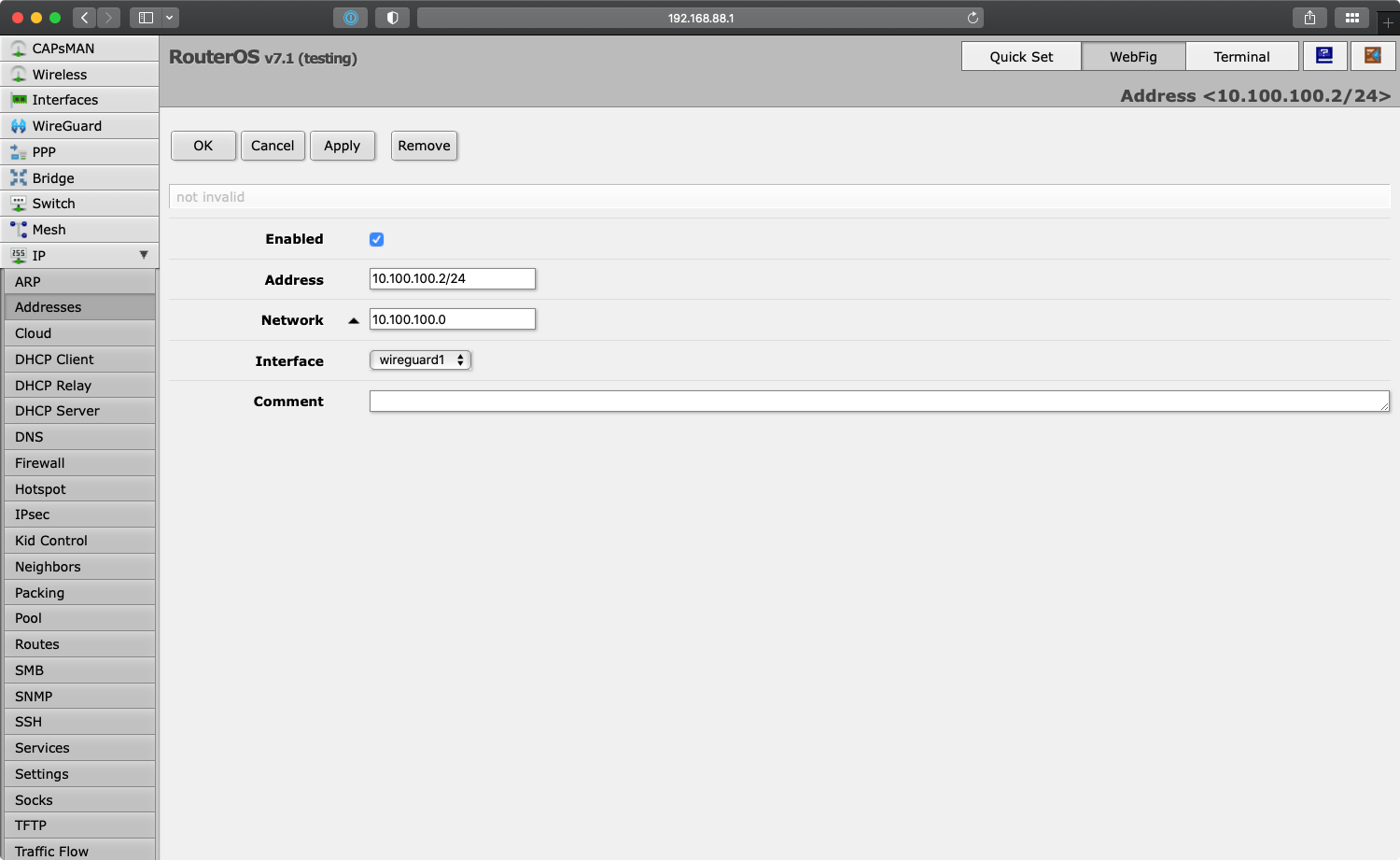
10.100.100.2/24 to RouterOS.Under “Interface” select the newly created WireGuard interface.
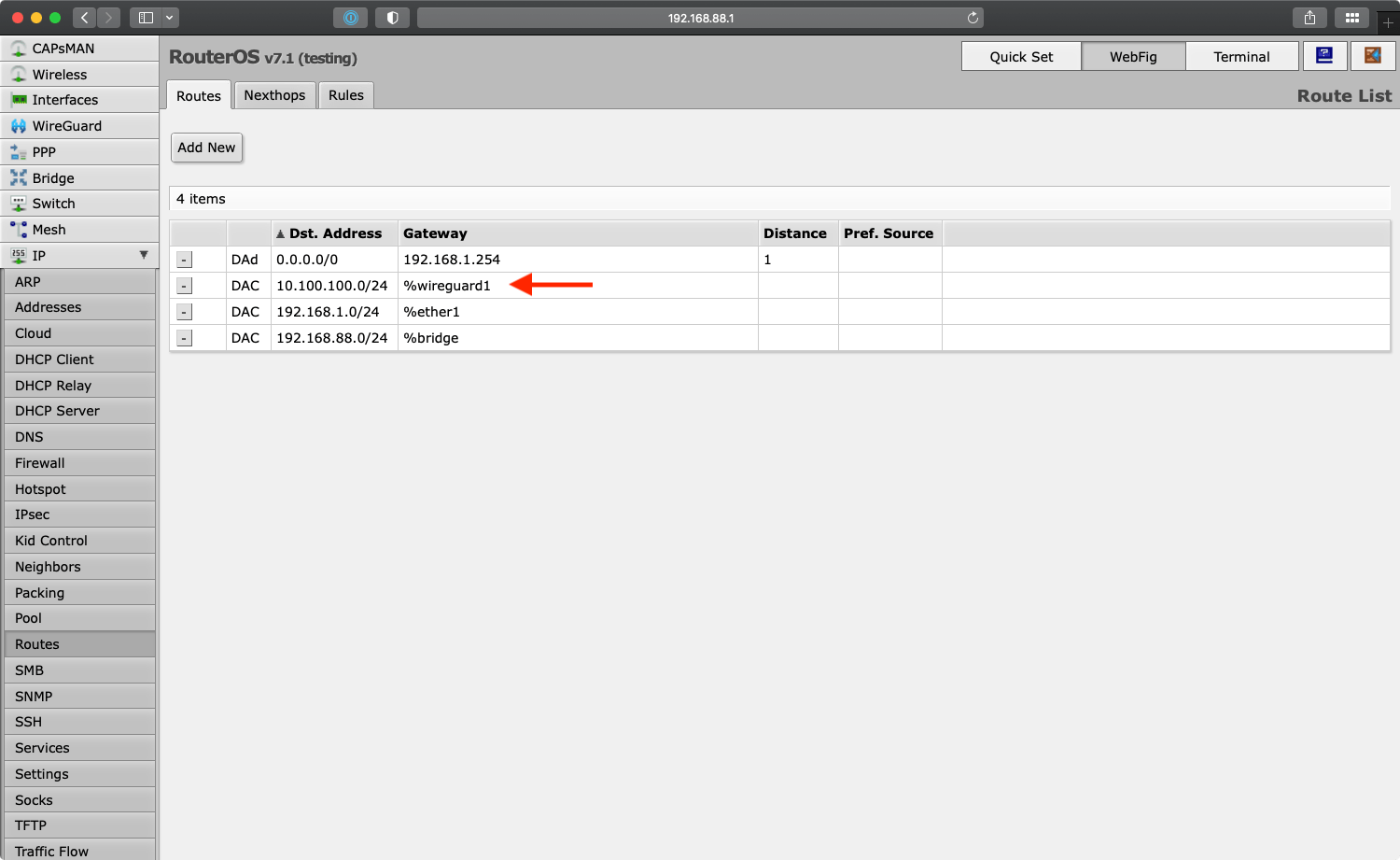
Notice how this automatically provisioned a new network route for 10.100.100.0/24 under “IP > Routes”:
Define WireGuard Network Firewall Rules
Finally, you need to add the firewall rules to match your desired configuration and access restrictions. See the RouterOS documentation page for a few examples.
Great guide. Thank you so much.
I would like to ask how do you configure the WireGuard network interface traffic graph? I don’t see on my Mikrotik.
Thank you.
I’m seeing the link to the Wireguard interface graph listed at the
/graphs/endpoint of Webfig after clicking on “Graphs” in the main menu above the “End-User License” item. I don’t remember enabling it so it should be there by default.